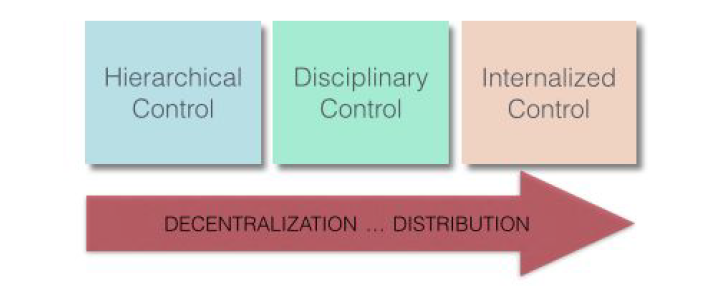
The paradox of control lies in how giving it away can acquire more of it. Rather than acquiring and retaining control through normal means, decentralized and distributed control actually relinquishes control to the populace. While decentralizing pushes control downwards, distribution makes control subversive. Decentralizing control by pushing it down in a hierarchy enables control in greater quantity and quality than allowed in a traditional command and control hierarchy. One effect of this is since the people that are closest to the problem have more intimate knowledge about the environment they end up making quicker decisions. While decentralized control requires a certain amount of observation1 , distributed control allows people to act completely autonomously so long as they have already internalized certain disciplinary rules. The final effect is a kind of totalitarianism2, where not only the public but even the private thought is controlled. Decisions are then acted upon completely asynchronously, and therefore more efficiently.
Command and Control < Discipline < Internalization
At the core of decentralization is a system of rules and prohibitions that instill discipline through voluntary obedience. That is to say that people agree to following the rules until the rules (in the distributed phase) become second nature. The rules become internalized only if they are presented properly and only after a certain amount of repetition. The three stages of control in history can be presented as follows:
1. The first (Hierarchical Command and Control) stage is a generalization of feudalistic control. An example of this stage would be the brutal idea of being shot for purposefully parking in a no parking zone. A central planner is needed to enact the punishment, preferably in a public setting for this type of control to be effective.
2. The second ( Discipline ) stage would be receiving training during the process of getting a driver’s license about no-parking signs, along with threat of constant observation and a fine for violating the rules. This marks the development of a deliberate and rational decision to obey results from weighing the value of the threat (enforced by observation) versus the value of the prohibited action.
3. The third ( Internalization ) stage is when the rational disciplinary decision becomes an unconscious decision, which is misrecognized as the person’s own willful decision. An example of this stage would be when local residents elect to have speed bumps installed in order to slow traffic. The driver elects to slow down when traversing the speed bumps and assumes this decision as their own natural way of navigating the environment.
Given this process, a question arises as to what kind of rules are needed to develop a distributed system? The creation of a distributed control system requires the development of rules in three separate domains: ethical, interpellatory, and autonomical.
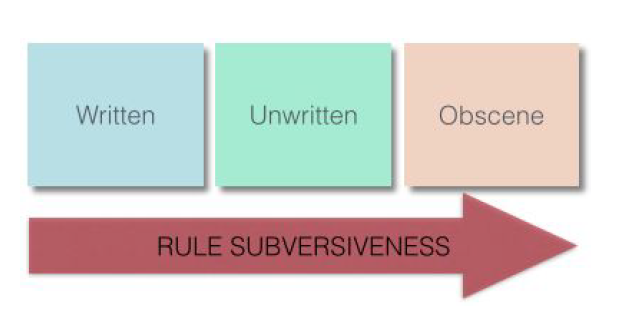
The ethical domain is established through prohibitions. These can be written (e.g. legal) rules, unwritten (partially known, or unconscious e.g. grammar) rules, or obscene (unmentionable, e.g. the emperor has no clothes) rules. As a rule becomes more concealed it becomes easier to internalize3 . Normally a rule-prohibition
is established through repetitive propaganda, advertising, or other rhetorical techniques directed at the public. An example of a subversive unwritten rule would be patriotism or jingoism (that one should have an emotional attachment to one’s country, possibly to the aggressive exclusion of other countries). When there is a voluntary military at peacetime (versus a drafted military), it is generated through patriotism, jingoism, or conversely the prohibition against being a traitor.
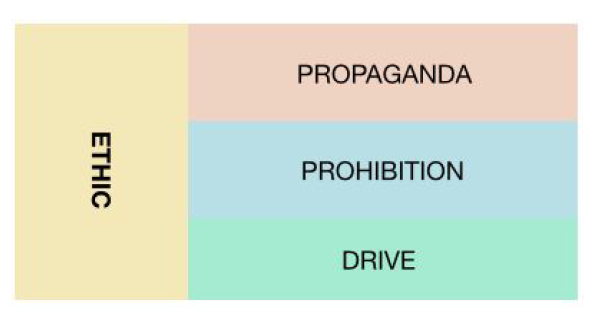
Rational + Ethical > Convenience
In order to decide on what ethical prohibitions to establish, there must be an investigation into what is utilitarian. We know from Steve Pink that we are driven by monetary reasons, but also autonomy, mastery, and purpose4 . Since prohibitions and drivers can be 4 made into closely related couples (monetary compensation/being cheated, autonomy/coercion, mastery/amateurism, purpose/uselessness) either side can be picked for the propaganda phase. It should be noted that prohibitions are used more often than solicitations when communicating ethics (e.g. U.S Legal Code). Once a rational and ethical prohibition is decided upon it must be communicated through repetitive advertising. Economic convenience emerges when the population responds to the rational and ethical propaganda. An example of economic convenience is the advertising of the benefits of ridesharing within the sharing economy5, and then the realizing of increased business by Uber.
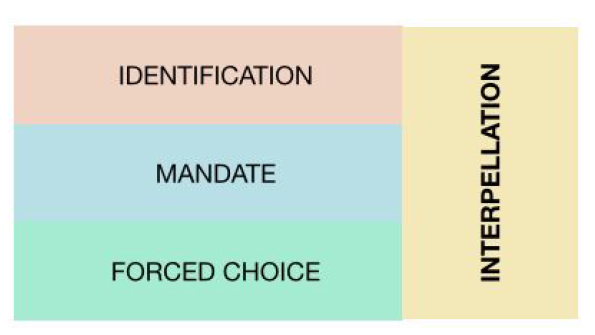
Forced Choice >Persuasion
In order to control autonomy, a persuasive technique must be used. A subtle punishment makes for a persuaded choice. This punishment can be in the form of shaming the violation of an established ethic, such as the propagandized ethic mentioned previously. Such a shaming technique is used within the idea of a forced choice. A forced choice is presented when the option to choose from multiple options is encouraged, but a “right” option is also encouraged. The forced choice creates pressure to choose the “right” option just by the fact that a choice is presented. An example of a forced choice would be a father telling the child “You know your grandmother loves you very much. She would love to see you. You don’t have to see her if you don’t want to. Would you like to visit her?”6. An individual that
succumbs to such a forced choice soon begins to identify with their decision. When someone asks ‘Are you a patriot?’ the implicit, obscene, and opposite question ‘Are you a traitor?’ is also implied, which is the hidden, pressure-creating underside that makes the question a forced choice. After the patriot option is freely chosen a person then begins to identify as a patriot. Through identification the subject may even forget having chosen to be a patriot and come to think of themselves as always having some latent, innate patriotism. This whole process sets the stage for someone to paradoxically act freely within the constraints of an ideological mandate set up by the forced choice. The end result of this process is people end up being persuaded into making decisions that may be against their best interests.
Interpellation >Identification >Mandate >Forced Choice
After an ethical stance is communicated and that communication is interpellated into a person, the result is a paradoxical autonomous obedience. When the western world transitioned from feudalism to modern capitalism there was another, more subversive, transition. This transition was from the traditionalist to the postmodernist world view of power. There are really three transitions here. From traditional hierarchical power (via threat of punishment)7, to modernist power (via implementation of discipline)8 , to postmodernist distributed 8 control. The modernist form of power is described by Foucault as:
“… creating and sustaining a power relation independent of the person who exercises it; … To achieve this, it is at once too much and too little that the prisoner should be constantly observed by an inspector: too little, for what matters is that he knows himself to be observed; too much, because he has no need in fact of being so. In view of this, Bentham laid down the principle that power should be visible and unverifiable.”9
Hence, Foucault has the modern form of power as being centered around the paradoxical threat of observation. The paradox here being if you are merely being watched, there is no threat (unless you have something to hide).
Within distributed control, observation is reduced or eliminated. One example of this stage of control is codified in what Alexander Galloway calls protocol:
“Protocol is a system of distributed management that facilitates peer-to-peer relationships between autonomous entities.”10
While protocol is exemplified in graph like structures like TCP/IP, it should be noted that Galloway says that protocols are:
“… more than simply a synonym for ‘the rules’ … protocol is like the trace of footprints left in snow … One is always free to pick a different route. But protocol makes one instantly aware of the best route11…“ So with a protocol system of management the incentive is internalized in the rules: “… [when] local residents elect to have speed bumps installed … Driving slower becomes advantageous … the driver wants to drive more slowly … it becomes a virtue to drive slowly.12”
Incentive, salience, and the ability to opt out from participation all capture the essence of the subversive distributed form of power.
Examples
While distributed control has not yet permeated all of societies’ social groups, there are some current examples of subversive, distributed control.
● Bitcoin Centralization
Bitcoin is an incentive compatible peer to peer electronic currency. The security of Bitcoin is based on having ‘honest nodes’ control the network:
“The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.”13
There have been issues with the centralization14 of the owners of nodes which is opposed to the spirit of having ‘honest nodes’ control the network. This is because of an inherent problem related to resources accruing an economy of scale that forbids smaller nodes or coalitions from entering into the competition for ownership. If this centralization affect continues, the mere appearance of distribution and trust-lessness creates an incentive for participants to voluntarily use Bitcoin as a currency, even though the owners of the nodes may no longer be honest.
● The Office Open XML document standard
Standards bodies have often been used to coordinate development of technologies into standards so that organizations and individuals can implement the new technology. A standards body with good name recognition such as the ECMA promotes trust and protects against harmful anticompetitive
practices15. During the development of the Office Open XML standard, the various rhetorical16 and strategic devices were used that compromised the development of the standard17. The result was a centralizing of control in the hands of a few, while retaining the appearance of an open standard. With the openness of the standard compromised, the users that exchange documents using the standard further the power of a centralized power structure through network effects18
Great Centralized Power >Decentralization, Distribution
Paradoxically, great centralized power has its reach extended by decentralization19 and its intentions masked by distribution. In order to address the decentralized manifestation of power, we ought to limit the amount of observation that the general populace is subject to. To address the power in distribution, we ought to prefer those equilibriums in ownership and standards that represent the flatter hierarchies . It remains to be seen whether addressing either of these problems can actually be implemented with a long term solution.
- Foucault, Michel (2012-04-18). Discipline & Punish: The Birth of the Prison (Vintage) p. 201. Knopf Doubleday Publishing Group. Kindle Edition. “The major effect of the Panopticon: to induce in the inmate a state of conscious and permanent visibility that assures the automatic functioning of power. So to arrange things that the surveillance is permanent in its effects, even if it is discontinuous in its action; that the perfection of power should tend to render its actual exercise unnecessary.”
- https://en.wikipedia.org/wiki/Totalitarianism
- Foucault, Michel (2012-04-18). Discipline & Punish: The Birth of the Prison (Vintage) p. 218. Knopf Doubleday Publishing Group. Kindle Edition. “But the peculiarity of the disciplines is that they try to define in relation to the multiplicities a tactics of power that fulfils three criteria: firstly, to obtain the exercise of power at the lowest possible cost (economically, by the low expenditure it involves; politically, by its discretion, its low exteriorization, its relative invisibility, the little resistance it arouses).”
- Pink, Daniel H. (2011-04-05). Drive: The Surprising Truth About What Motivates Us, Penguin Publishing Group. Kindle Edition, Locations 941-945. “Many theories of behavior pivot around a particular human tendency: We’re keen responders to positive and negative reinforcements, or zippy calculators of our self-interest, or lumpy duffel bags of psychosexual conflicts. SDT, by contrast, begins with a notion of universal human needs. It argues that we have three innate psychological needs—competence, autonomy, and relatedness. When those needs are satisfied, we’re motivated, productive, and happy. When they’re thwarted, our motivation, productivity, and happiness plummet.”
- http://time.com/3923031/uber-lyft-carpooling/
- Žižek, Slavoj (2007). How to Read Lacan, W. W. Norton & Company, p. 92.
- https://en.wikipedia.org/wiki/Discipline_and_Punish#Torture
- https://en.wikipedia.org/wiki/Discipline_and_Punish#Discipline
- Foucault, Michel (2012-04-18). Discipline & Punish: The Birth of the Prison (Vintage) p. 201. Knopf Doubleday Publishing Group. Kindle Edition.
- Galloway, Alexander. Protocol: How control exists after decentralization, Cambridge, MA: The MIT Press, 2004, p. 243.
- Galloway, Alexander. Protocol: How control exists after decentralization, Cambridge, MA: The MIT Press, 2004, p. 244.
- Galloway, Alexander. Protocol: How control exists after decentralization, Cambridge, MA: The MIT Press, 2004, p. 241.
- https://bitcoin.org/bitcoin.pdf, Bitcoin: A Peer-to-Peer Electronic Cash System, Satoshi Nakamoto.
- http://blog.dshr.org/2014/10/economies-of-scale-in-peer-to-peer.html
- https://en.wikipedia.org/wiki/Embrace,_extend,_and_extinguish
- https://en.wikipedia.org/wiki/Standardization_of_Office_Open_XML#Complaints_about_the_national_bodies_process
- https://en.wikipedia.org/wiki/Standardization_of_Office_Open_XML#Post-adoption_quotes
- https://en.wikipedia.org/wiki/Network_effect
- Foucault, Michel (2012-04-18). Discipline & Punish: The Birth of the Prison (Vintage) p. 206. Knopf Doubleday Publishing Group. Kindle Edition. “In each of its applications, it makes it possible to perfect the exercise of power. It does this in several ways: because it can reduce the number of those who exercise it, while increasing the number of those on whom it is exercised. Because it is possible to intervene at any moment and because the constant pressure acts even before the offences, mistakes or crimes have been committed.”
